What Is a Security Operations Center (SOC)?
In today’s rapidly evolving threat landscape, organizations face unprecedented challenges in protecting their digital infrastructure.
Cyberattacks have grown in both frequency and sophistication, forcing enterprises to adopt proactive, intelligent, and integrated defense mechanisms. At the heart of these efforts lies the Security Operations Center (SOC), a mission-critical hub that monitors, detects, and responds to security incidents around the clock.
Increasingly, SOCs are evolving beyond traditional monitoring centers to become data-driven, AI-assisted command centers. Platforms like SmartSuite, with its enterprise-ready Cybersecurity and GRC Solution Suites, are enabling this transformation, connecting data, automating workflows, and empowering security teams to operate with speed, intelligence, and confidence.
Key Takeaways
- Assess Your Security Posture: Determine your maturity level, compliance obligations, and business risk to select the right SOC model.
- Unify Data and Processes: Integrate SOC operations with enterprise workflows for risk management, compliance, and resilience using a platform like SmartSuite.
- Leverage AI and Automation: Use intelligent automation to reduce noise, improve detection accuracy, and accelerate response times.
- Commit to Continuous Improvement: Regularly review SOC processes, update playbooks, and evolve with emerging threats.
The Basics of a Security Operations Center (SOC)
A Security Operations Center (SOC) is a centralized team and facility responsible for safeguarding an organization’s information assets. Its mission is to monitor, detect, analyze, and respond to cybersecurity incidents in real time. A modern SOC operates 24/7, ensuring continuous vigilance and rapid response to potential threats that could compromise critical systems or data.
The SOC’s core objective is to uphold the confidentiality, integrity, and availability (CIA) of enterprise data, protecting digital assets from internal misuse, external attacks, and systemic vulnerabilities.
Key Components of a SOC
People
Highly skilled professionals, cybersecurity analysts, threat hunters, and incident responders, are the backbone of every SOC. They analyze alerts, investigate anomalies, and coordinate remediation actions.
Processes
Standardized workflows ensure that threat detection, triage, and response activities follow consistent and repeatable steps. These are often codified in runbooks and playbooks that define response procedures for various attack scenarios.
Technology
Advanced technologies such as Security Information and Event Management (SIEM) systems, Intrusion Detection Systems (IDS), Endpoint Detection and Response (EDR), and now, AI-assisted threat analysis tools, form the technological foundation of modern SOCs.
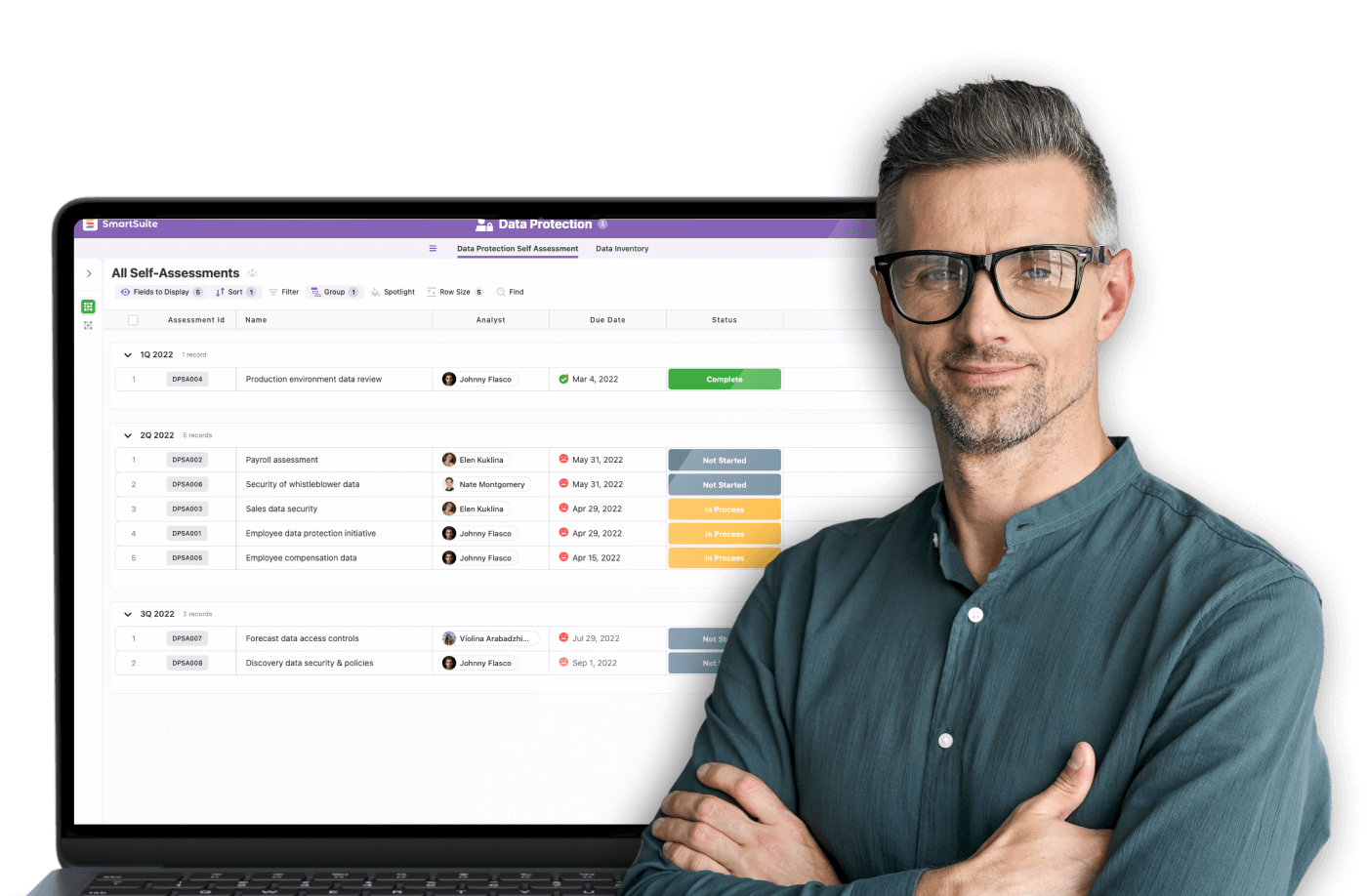
With SmartSuite, organizations can connect SOC processes to their broader governance, risk, and compliance (GRC) framework, creating a unified system that links incident management, risk assessment, and regulatory reporting on a single AI-powered platform.
The Evolution and Importance of SOCs
Why SOCs Are Essential in Modern Cybersecurity
As digital ecosystems expand, the traditional perimeter-based approach to cybersecurity has become obsolete. SOCs provide a centralized and coordinated defense strategy, combining human expertise, automation, and analytics to secure the organization in real time.
For example, a financial institution might rely on its SOC to continuously monitor high-value transactions and detect unauthorized access patterns. SmartSuite’s Cybersecurity Suite enhances this capability by integrating risk registers, incident workflows, and automated alert routing,ensuring that security events translate into structured responses and compliance documentation.
How SOCs Have Evolved
Historically, SOCs were reactive, responding only after a breach occurred. Today, the paradigm has shifted to proactive and predictive defense. Modern SOCs leverage AI, machine learning, and threat intelligence to anticipate and prevent attacks before they manifest.
SmartSuite plays a pivotal role in this evolution. Its AI-driven automation engine can trigger immediate workflows when anomalies are detected, from creating incident records and notifying stakeholders to initiating forensic reviews and compliance checks. By integrating SOC data into broader IT Service Management (ITSM) and Business Resilience workflows, SmartSuite enables organizations to manage cybersecurity as a seamless part of enterprise operations.
SOC Operations and Best Practices
Core Functions of a SOC
- Continuous Monitoring: Tracking network activity, endpoint behavior, and system logs for suspicious patterns.
- Incident Response: Executing predefined playbooks to contain and remediate threats swiftly.
- Threat Intelligence: Leveraging internal and external data sources to identify new vulnerabilities or attack vectors.
- Vulnerability Management: Continuously scanning and prioritizing system weaknesses for remediation.
With SmartSuite’s platform, SOC teams can link each of these functions to structured workflows, ensuring that alerts escalate automatically, tasks are assigned to responsible analysts, and actions are documented for audit readiness.
Implementing SOC Best Practices
- Define Clear KPIs: Metrics such as Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR) are critical to evaluating SOC performance. SmartSuite’s analytics dashboards give leaders real-time visibility into these metrics.
- Invest in Training and Simulations: Regular red team exercises and simulated attacks build team readiness. SmartSuite supports these efforts by managing training plans, tracking skill assessments, and storing lessons learned within the same ecosystem.
- Adopt Automation and AI: Automation reduces alert fatigue by prioritizing the most critical incidents. SmartSuite’s intelligent workflows use AI to triage and route incidents based on context, freeing analysts to focus on complex, high-impact threats.
SOC Models and Use Cases
In-House vs. Outsourced SOC
Organizations may choose between building an in-house SOC or leveraging a Managed Security Service Provider (MSSP).
- In-House SOCs: Offer control and customization, ideal for enterprises with sensitive data or strict compliance needs.
- Outsourced SOCs: Provide scalability and access to specialized expertise, often at lower cost.
SmartSuite’s modular architecture supports both models, enabling MSSPs to manage multiple client environments securely, or enterprises to operate their own SOCs with integrated governance and automation.
Real-World Use Cases
- Healthcare Institutions: Protecting patient data from ransomware by linking detection events directly to SmartSuite’s Compliance Suite for HIPAA response tracking.
- Financial Services: Automating incident reporting workflows to ensure alignment with regulatory requirements like SOX and PCI DSS.
- Retail Enterprises: Monitoring POS and e-commerce systems for fraud while integrating findings into enterprise risk dashboards.
The Future of SOC
Emerging Trends
The SOC of the future is AI-powered, integrated, and collaborative. Advances in large language models, threat intelligence fusion, and automated playbook execution are redefining what SOCs can achieve.
SmartSuite is leading this convergence by embedding AI across its platform, from automated detection and response recommendations to natural language querying of risk and incident data. This allows CISOs and analysts to move from reactive defense to predictive security.
Challenges and Solutions
- Talent Shortage: SmartSuite mitigates staffing challenges by automating manual tasks, documenting repeatable processes, and providing centralized dashboards that simplify management.
- Alert Fatigue: SmartSuite’s AI models can help prioritize alerts based on impact and risk context, ensuring teams focus on what matters most.
Conclusion
A Security Operations Center is more than just a defensive unit, it’s the command hub of modern cyber resilience. To remain effective, SOCs must evolve alongside the threats they counter, embracing AI, automation, and integration across enterprise systems.
SmartSuite’s AI-powered platform enables organizations to achieve exactly that, connecting security operations with governance, risk management, compliance, and resilience in one unified environment. Whether operating an internal SOC or partnering with external providers, SmartSuite delivers the visibility, automation, and intelligence enterprises need to stay secure in a dynamic digital world.
Get started with SmartSuite Governance, Risk, and Compliance
Manage risk and resilience in real time with ServiceNow.



