What Is Penetration Testing?
In an era where cyber threats are increasingly sophisticated, penetration testing emerges as a crucial component of an organization’s cybersecurity strategy.
But what exactly is penetration testing, and how does it fortify an organization's defenses against potential cyber attacks? This article delves into the intricacies of penetration testing, providing actionable insights and guidance for organizations seeking to bolster their security posture.
TL;DR
- Penetration testing basics simulate real-world attacks to uncover vulnerabilities and strengthen an organization’s security posture.
- Effective testing practices include clear objectives, skilled testers, regular assessments, and comprehensive reporting to stay ahead of evolving threats.
- SmartSuite streamlines pen testing by centralizing test management, automating remediation workflows, integrating security tools, and providing AI-driven insights.
The Basics of Penetration Testing
Penetration testing, often referred to as "pen testing," is a simulated cyber attack against your systems to evaluate the security of your IT infrastructure. It involves the use of various techniques to probe and identify vulnerabilities in a system before they can be exploited by actual cyber criminals.
The Process of Penetration Testing
Conducting a penetration test involves several key steps:
- Planning: Define the scope and goals of the test, determining which systems will be tested and how.
- Reconnaissance: Gather intelligence on the target system to identify potential vulnerabilities.
- Scanning: Analyze the target to locate live hosts and detect open ports.
- Gaining Access: Attempt to exploit identified vulnerabilities and gain access to the system.
- Maintaining Access: Test the ability to persist in the system while maintaining a foothold for future use.
- Analysis: Examine the results to pinpoint vulnerabilities, strategies for mitigation, and the potential impact on business operations.
Types of Penetration Testing
Several types of penetration testing cater to different security needs:
Black Box Testing
This form mimics an external cyber attack without prior knowledge of the internal workings of the target system.
White Box Testing
Contrary to black box testing, this involves complete knowledge of the system’s architecture, simulating an insider’s perspective.
Grey Box Testing
A hybrid approach where testers have partial knowledge of the system, striking a balance between insider knowledge and external analysis.
Why Penetration Testing is Essential
Conducting regular penetration tests provides organizations with a host of benefits:
- Identification of Vulnerabilities: Uncover security weaknesses in your systems before hackers do.
- Compliance and Regulations: Meet industry regulations such as PCI-DSS, GDPR, and HIPAA by demonstrating proactive security testing.
- Risk Management: Prioritize vulnerabilities based on their potential impact and likelihood of exploitation.
- Enhancement of Security Policies: Improve existing security measures and policies through insights gained from test results.
Penetration Testing in Action
Imagine a cloud services company that holds sensitive client data. By conducting a white box penetration test, they uncover a vulnerability in their data transmission protocols. This insight allows the company to patch the vulnerability, ensuring data integrity and maintaining client trust.
Best Practices for Effective Pen Testing
To ensure that your penetration testing efforts are fruitful, adhere to these best practices:
- Define Clear Objectives: Have a clear understanding of what you want to achieve with the test.
- Choose the Right Tools: Utilize reputable and comprehensive tools that simulate a wide range of attack vectors.
- Experience Matters: Engage experienced testers who understand the complexities of cybersecurity.
- Regular Testing: Make penetration testing a routine part of your cybersecurity strategy, rather than a one-time affair.
- Comprehensive Reporting: Document all findings meticulously and provide actionable recommendations for improvement.
The Future of Penetration Testing
With cyber threats becoming more advanced, penetration testing is evolving to keep pace. Automated penetration testing tools are gaining traction, allowing for quicker and more efficient identification of vulnerabilities. Additionally, leveraging artificial intelligence in testing scenarios offers promising avenues for predictive analytics in threat detection.
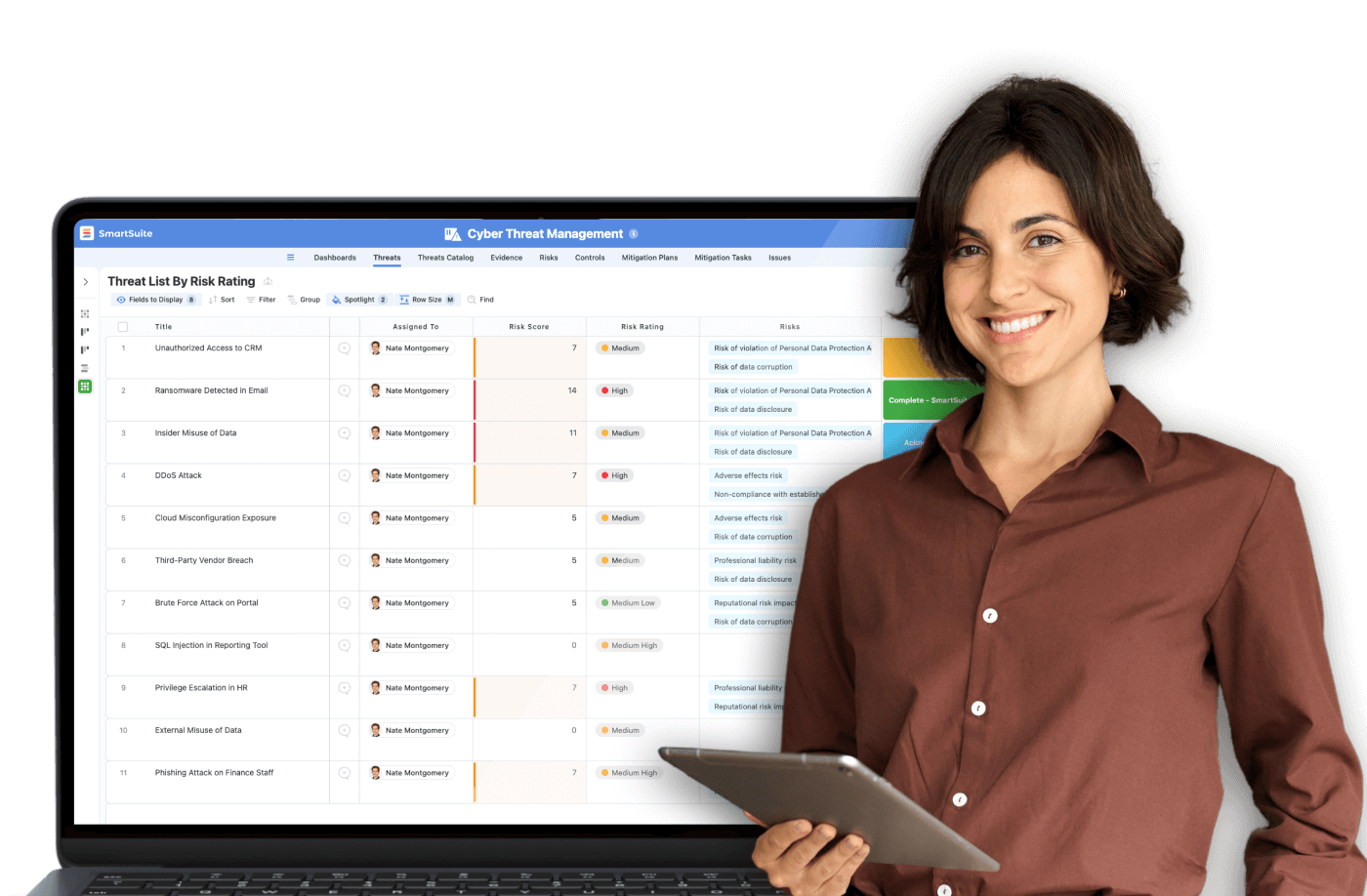
How SmartSuite Enhances Penetration Testing Management
SmartSuite elevates penetration testing from a periodic exercise to a continuous, data-driven component of an organization’s cybersecurity lifecycle. By integrating test management, reporting, and remediation tracking into a single, unified platform, SmartSuite enables teams to plan, execute, and act on penetration test results with greater speed, visibility, and accountability.
Centralized Test Management and Collaboration
SmartSuite serves as a command center for managing penetration testing programs. Security teams can log test scopes, track schedules, assign responsibilities, and collaborate across departments, all within one intuitive workspace. This centralization ensures that every phase, from planning to post-test analysis, remains transparent and well-documented.
Automated Workflows for Remediation Tracking
Once vulnerabilities are identified, SmartSuite’s workflow automation instantly routes remediation tasks to the appropriate owners. Teams can set deadlines, assign priorities, and monitor progress in real-time. Automated alerts and reminders ensure that critical vulnerabilities are never overlooked, and that remediation efforts align with organizational security objectives.
Seamless Integration with Security Tools
SmartSuite integrates with leading vulnerability scanners, security orchestration (SOAR) systems, and reporting tools. This integration consolidates findings from multiple testing environments, network, web, and application layers, into a single view. Security data flows directly into SmartSuite dashboards, streamlining analysis and enabling faster, coordinated responses.
AI-Powered Insights and Prioritization
Using AI Assist, SmartSuite analyzes test data to identify recurring vulnerability patterns, categorize risks by severity, and recommend targeted mitigation actions. It can also generate executive-ready summaries, providing clear rationales behind each recommendation for improved transparency and decision-making.
Comprehensive Reporting and Audit Readiness
SmartSuite’s dynamic dashboards transform complex penetration test data into actionable intelligence. Teams can generate customizable reports for technical teams, auditors, or executives, complete with real-time metrics, visualizations, and compliance mappings for frameworks such as NIST, ISO 27001, and SOC 2.
The Result: SmartSuite transforms penetration testing into a strategic, repeatable, and measurable process, ensuring every test leads to tangible improvements, documented compliance, and a stronger, more resilient security posture.
Conclusion
In an era where cyber threats evolve daily, penetration testing is no longer a one-time exercise, it’s an ongoing commitment to resilience. By simulating real-world attacks, organizations can uncover hidden vulnerabilities, validate security controls, and strengthen their defenses before malicious actors strike.
When managed through SmartSuite, penetration testing becomes more than a diagnostic measure, it transforms into a living, iterative process embedded within the broader cybersecurity ecosystem. SmartSuite’s automation, AI insights, and integrated workflows turn complex test results into coordinated remediation actions, ensuring that every vulnerability leads to measurable improvement.
Get started with SmartSuite Governance, Risk, and Compliance
Manage risk and resilience in real time with ServiceNow.



