What Is Threat Intelligence?
In today’s rapidly evolving digital landscape, organizations are increasingly focusing on strengthening their cybersecurity measures to protect critical assets.
At the forefront of these measures is the utilization of threat intelligence. This powerful approach not only helps predict potential threats but also empowers organizations to proactively mitigate risks.
In this article, we will delve into the concept of threat intelligence, exploring its components, benefits, and implementation strategies as part of a comprehensive cybersecurity framework.
TL;DR
- Threat intelligence fundamentals help organizations predict attacks and strengthen cybersecurity by analyzing threat data across strategic, tactical, operational, and technical levels.
- Proactive defense strategies use threat intelligence to enhance incident response, manage risks, and protect industries like banking, healthcare, and IT.
- SmartSuite elevates threat intel by unifying feeds, automating response workflows, integrating with security tools, and turning insights into coordinated action.
The Basics of Threat Intelligence
Threat intelligence refers to the collection and analysis of information about current or potential attacks that may threaten an organization's systems. This intelligence helps in making informed security decisions, enabling proactive defense measures, and ultimately improving security postures.
Threat intelligence can be classified into different types based on its application scope and usage:
1. Strategic Threat Intelligence
Strategic threat intelligence delivers insights at a high level, providing macro-level trends and patterns that can inform management and executive decisions. This type of intelligence often includes:
- Industry Reports: Analyzing trends within industries, such as finance or healthcare, to identify common threat vectors.
- Forecasting: Predicting future threats based on historical data and global intelligence.
2. Tactical Threat Intelligence
Tactical threat intelligence focuses on specific details about threats, such as the tools and techniques utilized by attackers. Key components include:
- Indicators of Compromise (IOCs): Data such as IP addresses, URLs, or email subjects that can suggest potential compromises.
- Attack Vectors: Information on the methods attackers use to breach systems.
3. Operational Threat Intelligence
Operational intelligence involves the identification and analysis of specific events and incidents. This real-time intelligence is crucial for immediate defense responses and includes:
- Malicious IP Addresses: Tracking IP addresses involved in attacks.
- Phishing Campaigns: Identifying ongoing phishing attempts to mitigate them promptly.
4. Technical Threat Intelligence
Focusing on the technical aspects, this intelligence involves data such as vulnerabilities and exploits that may be used against an organization’s infrastructure.
The Value of Threat Intelligence
Implementing an effective threat intelligence strategy offers numerous benefits:
Enhanced Incident Response
By having access to timely and accurate intelligence, security teams can respond more effectively and efficiently to security incidents.
Proactive Defense
Organizations can identify potential threats before they materialize, enabling them to implement preventive measures that deter attacks.
Improved Risk Management
Threat intelligence provides a clearer understanding of threats, allowing organizations to prioritize risks and allocate resources accordingly.
Increased Awareness
Regular updates on global threat landscapes keep security teams informed, helping them adapt their strategies to emerging challenges.
Applying Threat Intelligence: Use Cases
Use Case 1: Banking Sector
Banks and financial institutions face continuous threats ranging from phishing to sophisticated cyber attacks. Threat intelligence aids them in identifying fraudulent schemes and unauthorized transactions, safeguarding both their assets and customers' data.
Use Case 2: Healthcare
Healthcare organizations handle sensitive patient data, making them a prime target for cybercriminals. Through threat intelligence, these institutions can track ransomware threats and protect patient information.
Use Case 3: IT Management
For IT departments, threat intelligence helps maintain secure infrastructures by identifying vulnerabilities in software and systems, allowing timely patch management.
Best Practices for Threat Intelligence
- Continuous Monitoring: Regularly update and analyze threat data to stay ahead of evolving cyber threats.
- Cross-Departmental Collaboration: Foster communication between IT, security, legal, and management teams to streamline incident response.
- Vendor Partnerships: Engage with threat intelligence providers to access broader data sets and advanced threat analysis.
- Training and Awareness: Regular training sessions for employees to recognize threats and understand the importance of threat intelligence.
How SmartSuite Enhances Threat Intelligence Management
SmartSuite strengthens organizational cybersecurity by transforming threat intelligence into actionable, collaborative, and measurable processes. Through its integrated work management framework, SmartSuite connects security insights with operational workflows, ensuring that threat data not only informs decision-making but also drives real-time action across teams.
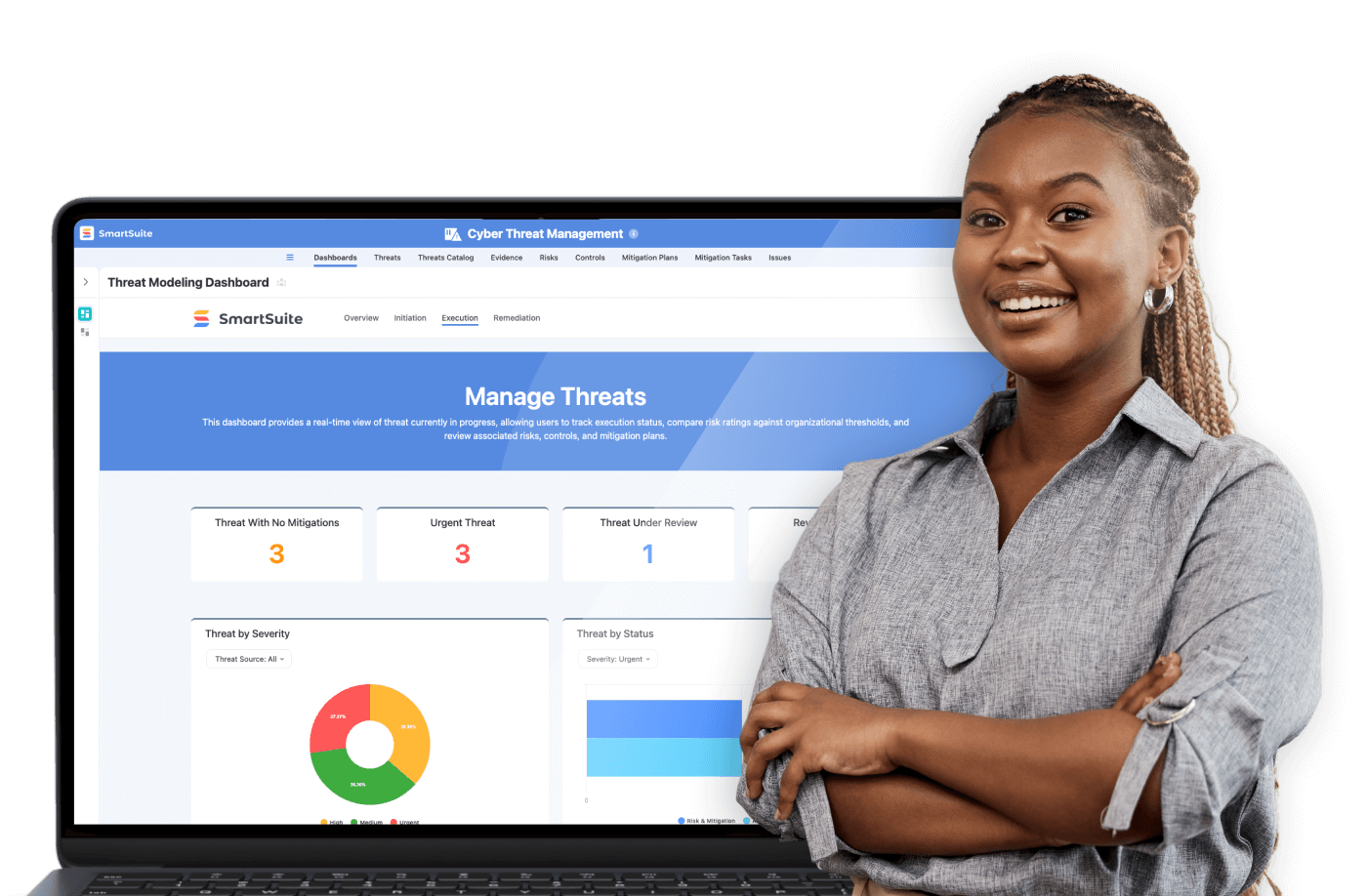
Unified Threat Intelligence Dashboard
SmartSuite consolidates multiple intelligence feeds into a centralized dashboard, offering security teams a unified view of potential risks, incidents, and emerging threat trends. This integrated visibility enables faster situational awareness and more accurate prioritization of responses.
Automated Response Workflows
When threat indicators or anomalies are detected, SmartSuite’s automation engine can instantly trigger workflows, creating incident tickets, assigning tasks to analysts, and escalating high-severity alerts to leadership. Automated notifications ensure that every identified threat is acknowledged and addressed without delay.
Integration with Security and Monitoring Tools
SmartSuite seamlessly integrates with SIEMs, SOAR platforms, and external threat intelligence sources. This bidirectional flow of data ensures that external intelligence feeds continuously update SmartSuite dashboards, while internal activity logs and incident responses feed back into the broader threat intelligence ecosystem.
AI-Powered Analysis and Predictive Insights
With AI Assist, SmartSuite enhances analysis by detecting patterns across historical threat data, helping teams identify potential attack vectors and emerging campaigns before they escalate. Predictive analytics highlight areas of elevated risk, guiding proactive defense measures.
Collaborative Investigation and Reporting
SmartSuite enables cross-departmental collaboration through shared workspaces, threaded discussions, and real-time document sharing. Analysts, IT staff, and compliance officers can investigate incidents together, attach forensic evidence, and build detailed audit trails, all within a secure environment.
Continuous Compliance and Governance Alignment
SmartSuite embeds threat intelligence insights into its GRC modules, ensuring that risk management, compliance, and security operations remain aligned. Automated reporting supports adherence to standards such as NIST, ISO 27001, and SOC 2, reducing administrative overhead while maintaining transparency.
The Result: SmartSuite transforms static threat data into dynamic, coordinated defense actions, enabling organizations to predict, prevent, and respond to cyber threats with speed, intelligence, and confidence.
Conclusion
In an era where cyber threats evolve faster than traditional defenses, threat intelligence stands as the foundation of a proactive cybersecurity strategy. It empowers organizations to move from a reactive stance to one of anticipation, predicting, preventing, and neutralizing risks before they impact operations.
By integrating threat intelligence into SmartSuite’s unified work management environment, organizations gain not only visibility but control. SmartSuite bridges the gap between intelligence and execution, transforming threat data into coordinated action, automated response, and continuous learning. Its AI-powered insights, seamless integrations, and cross-functional collaboration tools ensure that every alert, indicator, and vulnerability translates into measurable security outcomes.
Get started with SmartSuite Governance, Risk, and Compliance
Manage risk and resilience in real time with ServiceNow.



