Cyber Threat Management
Identify and assess cyber risks, track threats and vulnerabilities, and connect remediation actions directly to your risk framework for complete visibility.
Solution Overview
The Cyber Threat Management solution provides a unified workspace for identifying, tracking, and mitigating cybersecurity threats across your organization.SmartSuite consolidates vulnerability data, threat intelligence, and incident response activities to create a single, accurate view of cyber risk.
The solution aligns with industry frameworks such as NIST Cybersecurity Framework (CSF), ISO 27001, and the CRI Profile, enabling security and risk teams to map every vulnerability, control, and remediation plan to enterprise risk objectives.
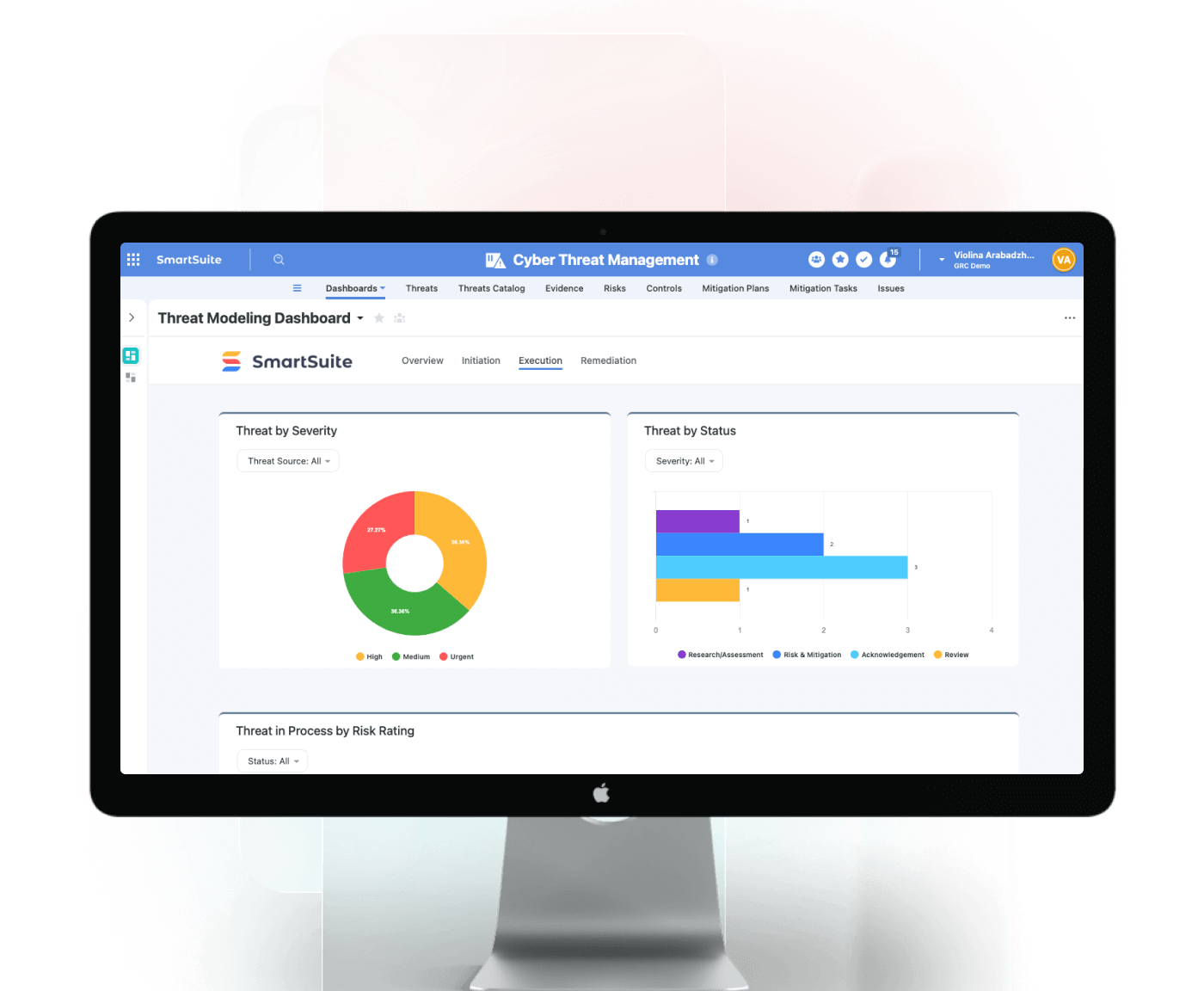
Real-time dashboards display active threats, open vulnerabilities, and mitigation progress — helping IT and security leaders continuously improve their cyber posture.

Core Capabilities
SmartSuite’s Cyber Threat Management solution combines risk governance with real-time security operations. It links technical findings to business impact so security leaders can prioritize what matters most.
Cyber Risk Register
Document and categorize threats, vulnerabilities, and assets with associated risk scores.
Threat & Vulnerability Tracking
Monitor open vulnerabilities and automatically link them to risk records.
Incident Correlation
Connect security events to impacted systems and trigger remediation tasks.
Framework Alignment
Map controls and risks to NIST CSF, ISO 27001, and CRI Profile domains.
Automated Remediation Workflows
Create tasks and notifications when threats exceed thresholds.
KRI & KPI Dashboards
Visualize cyber health metrics and open issues.
Audit Trail & Reporting
Generate board-ready reports showing trends, exposure, and closure rates.
The Cyber Threat Lifecycle
SmartSuite supports the entire cyber threat lifecycle — from identifying vulnerabilities to reporting remediation outcomes — all connected to enterprise risk records.
Identify Threats & Vulnerabilities
Ingest data from vulnerability scanners or threat feeds.
Assess & Prioritize
Evaluate likelihood and impact using risk scoring models.
Respond & Mitigate
Assign owners and track remediation plans to completion.
Monitor & Verify
Measure control effectiveness and track recurrence rates.
Report & Improve
Share cyber posture dashboards with leadership and audit teams.
Who Uses This Solution
The Cyber Threat Management solution supports security, IT, and risk professionals tasked with protecting information assets and maintaining compliance with industry standards.

Aligns cybersecurity risk management with enterprise governance and compliance goals.

Maintains the risk register and coordinates vulnerability and incident response.

Investigates threats and tracks mitigation progress.

Ensures third-party engagements meet internal policy standards and regulatory obligations across security, privacy, and operational domains.

Conducts testing, documents results, and reviews audit evidence.
Performs independent testing and validation of SOX controls.
Connected GRC Ecosystem
The Cyber Threat Management solution connects with other SmartSuite modules to provide a holistic view of technology risk and business impact.

Artificial Intelligence
SmartSuite's AI generates insights, summarizes complex results, and predicts risks within existing workflows to support proactive decisions.
AI Threat Pattern Detection
Automatically identify suspicious patterns, correlated indicators of compromise (IOCs), and anomalous activity across threat feeds, incidents, and vulnerability data.
AI Threat Pattern Detection
Automatically identify suspicious patterns, correlated indicators of compromise (IOCs), and anomalous activity across threat feeds, incidents, and vulnerability data.
Predictive Vulnerability Prioritization
Forecast which vulnerabilities or threat vectors are most likely to be exploited based on historical data, external threat intelligence, and internal asset context.
Automations
Use SmartSuite's no-code engine to eliminate repetitive tasks and ensure accountability across risk operations.
Automated Threat Intake & Routing
Automatically ingest threat indicators or vulnerability alerts and route them to the correct security analyst or response team based on severity and asset classification.
Investigation & Remediation Workflows
Trigger investigation tasks, evidence collection activities, and remediation plans when a threat is confirmed or a vulnerability reaches a defined risk threshold.
Notification & Escalation Rules
Send automated alerts to security teams, application owners, or executives when high-severity threats emerge or SLA deadlines are breached.
Integrations
Integrate with the tools your teams use every day. Keep controls, incidents, and risk data in sync through prebuilt connectors and open APIs.
SIEM & Monitoring Platforms
Integrate with Splunk, Datadog, Microsoft Sentinel, Elastic, or QRadar to ingest alerts, logs, and detection events into SmartSuite workflows.
Threat Intelligence Feeds
Connect to services like VirusTotal, Recorded Future, CrowdStrike Intel, or open-source feeds to centralize IOC and threat data.
Vulnerability Scanners & Ticketing Tools
Sync with tools such as Qualys, Tenable, Rapid7, Jira, and ServiceNow to capture vulnerabilities, assign remediation owners, and track resolution progress.


Frequently Asked Questions
Answers to common questions about SmartSuite’s pricing models, plan options, and onboarding programs.
Yes — it connects with vulnerability scanners, SIEM systems, and ticketing tools to automate cyber risk tracking.
Yes — controls can be tagged and mapped to multiple framework domains for reporting and auditing.
Yes — automations can ingest scanner outputs and create linked risk records.
All data is encrypted in transit and at rest, and access is governed by role-based permissions and audit logging.
Explore the SmartSuite GRC Suite
Strengthen your security posture and connect cyber risk management to your broader governance and compliance programs with SmartSuite’s integrated GRC Suite.